SPRCHRGR Verify App
Engineer Fraud Out of Your Approval Workflows
SPRCHRGR’s Verify App protects your cash and confidential financial data using proprietary bank-grade authentication security protocols — transforming verification from a bottleneck into a fraud-prevention firewall.
.png?width=1200&name=Verify%20App%20Hero%20Data%20Secure%20(1085%20x%20760%20px).png)
High-Growth Companies Are Prime Targets
Every week, hundreds of requests are exchanged: expense approvals, budget changes, vendor payments, payroll deposits, etc. Each one arrives via email. Each one assumes trust. One spoofed message can cost thousands and destroy years of relationship equity.
Too many lower-middle-market companies and SMBs believe they're "too small" to be targeted. They're wrong. Fraudsters specifically target businesses in the $3M-$50M range because they have significant cash flow but often lack enterprise-grade security protocols.
A Growing Problem:
- $16.6 billion lost to cybercrime in 2024 (+33% from 2023) [1]
- 63% of organizations are targets of Business Email Compromise (BEC) fraud [2]
- 79% of organizations experienced attempted or actual payment fraud attacks [2]
- 45% of organizations experienced vendor impersonation fraud (up from 34% in 2023) [2]
- $129,000 average loss per Business Email Compromise attack [1]
Sources:
[1] FBI Internet Crime Complaint Center (2024)
[2] Association for Financial Professionals Payments Fraud Survey (2025)
Three Common Methods Fraudsters Use to Hack Your Approval Process
Modern fraud isn't about breaking firewalls — it's about breaking trust. Fraudsters exploit gaps when humans respond to sensitive requests without proper verification. And these malicious threats are getting increasingly hard to spot with AI-enabled social engineering fraud.
The 'Urgent' CEO Message:
Your team receives an urgent message from the "CEO," via email, phone, or (even) live video. It looks real. It sounds like them. But is it?
The 'New Bank Info' Scam:
Did your vendor really change banks? Or did a hacker just intercept your AP report and use it to impersonate your vendor?
The 'Payroll Update' Scam:
An employee asks to update their direct deposit. Is it actually them, or a scammer who stole their identity?
/Sage%20Intacct%20and%20BQE%20Best%20of%20Both%20Worlds%20-%20Keep%20What%20Works_500x500.png?noresize&width=1200&height=1200&name=Sage%20Intacct%20and%20BQE%20Best%20of%20Both%20Worlds%20-%20Keep%20What%20Works_500x500.png)
Our Solution
Cybersecurity Protection Built into Your Human Approval Workflows
We’ve developed the SPRCHRGR Verify App to protect your business, at scale.
- Total Verification: We verify the authenticity of sensitive requests before responding — whether they come via email, phone, or text — using a proprietary MFA protocol.
- Human Hyper-Vigilance: While competitors automate your books with ungoverned AI (opening you up to errors and fraud), we use technology to empower your and our human experts to discretely defend against fakes.
- The 'Zero Trust' Standard: We treat every sensitive request as a potential threat until proven otherwise.
HOW IT WORKS
Integrated Requests and Approvals in One Unbreakable Chain of Verification
Step 1: Triage Request
- Our team receives a request (via phone, text, email, chat, online meeting, etc.) that could put your sensitive data or cash at risk
- Before responding, we pass it through our Verify App for you to authenticate

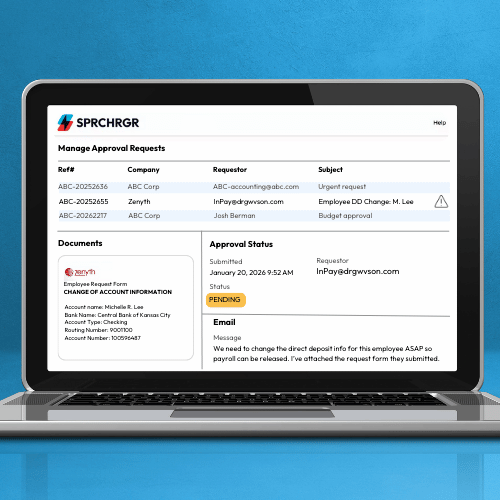
Step 2: Secure Notification
- Our system immediately notifies your designated approver(s)
- You access our secure portal to review and approve (or deny)
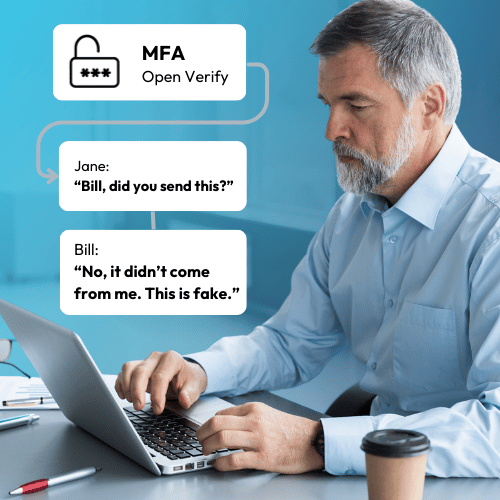
Step 3: Verified Approval
- Our team only proceeds after receiving your encrypted confirmation
- A complete audit trail is automatically maintained
Result: Fraud Prevented
- Spoofed emails and fraudulent activity stopped dead in their tracks
- You are in full control of each action
- Every transaction documented with IP addresses + timestamps
- Zero ambiguity about who authorized what





Enterprise-Grade Security — NOT AI Autopilot
SPRCHRGR brings a tech-forward approach that balances ease of automation with security. Here’s what you get with our Verify App:
Bank-Grade Authentication
Approvals are protected in a secure portal. Fraudsters can't circumvent using compromised accounts.
Document Security
Client approver(s) review sensitive correspondence and attachments within the portal. No unauthorized access or tampering possible.
Role-Based Control
Clients designate primary and delegate approvers. Your team always knows who has the authority to review and approve.
Complete Audit Trail
Every action logged: who submitted, who approved, when, and from what IP address. Compliance-ready documentation.
Confidential Dialogue
Keep sensitive internal discussions behind the firewall, where hackers can’t intercept.
Smart Notifications
Minimize email inbox clutter with customizable notification rules for each authorized user.
Our latest security + technology insights
/Cybersecurity%20for%20FinOps%20A%20Guide%20for%20Growth%20Stage%20Companies_1200x630.webp)
Article
Cybersecurity for Financial Operations: A Guide to Protect Your Data and Cash
In 2025, cybersecurity isn't just a technology problem — it's a boardroom problem. For growth-stage companies navigating fundraising, compliance, and M&...

Article
Finance Integration: 4 Myths That Keep CFOs Stuck in Manual Work
Despite the clear benefits of automation, many finance leaders remain stuck in manual processes — not because they don't see the value, but because they've...
/Sync%20Multi%20Entity%20Business%20Units%20Without%20ERP%20Headache%20Using%20Webhooks_1200x630.webp)
Article
How to Sync Multi-Entity Business Units (Without the ERP Integration Headache) Using Webhooks
As systems grow more complex and the volume of data increases, the old methods of manually transferring information from one platform to another simply no ...

Technology Solution
Custom API Syncs Paperless Vendor Bill Payments with AEC Industry Niche ERP Platform BQE CORE
An industry niche ERP software offers an all-in-one professional services automation platform with many available modules, from CRM + project management + ...

Secure Your Approval Process
Don’t leave your cash and reputation exposed. Get Started Today.
Existing clients have immediate access to the Verify App via your account manager. For everyone else, contact us to learn more!